· 10 min read
What permissions the PnP Management Shell app had in the past?
Reference to the API permissions the Entra ID app called "PnP Management Shell" had in the past used by community tools such as PnP PowerShell and CLI for Microsoft 365 when logging into the tenant as a human.

Introduction
There is a new change to the way a HUMAN connects to SharePoint using PnP PowerShell or the CLI for Microsoft 365 - the Entra ID enterprise app is going away and removed on the 9th September. Moving forward you will need to create your own Entra ID App to continue to perform operations using the tools in the future. This post is a reference to what this app had in the past once is goes away, so you can understand what permissions you need to request when creating your own app.
It is important to know that when you consider creating your own app, you may not need all the permissions that the Entra ID app had, so consider the permissions you need and only request those. You CAN always have more than one for different use cases and expanded scenarios.
All these permissions are DELEGATED permissions. This means to authenicate you need the USER or HUMAN to have permissions to the resource e.g. in the case of SharePoint, Site Collection Admin, SharePoint Admin, Site Member etc. AND the App will need permissions. This is the most restrictive way to authenticate and is recommended.
Screenshot of the App Permissions
Here is a screenshot of the permissions that the Entra ID app had in the past:
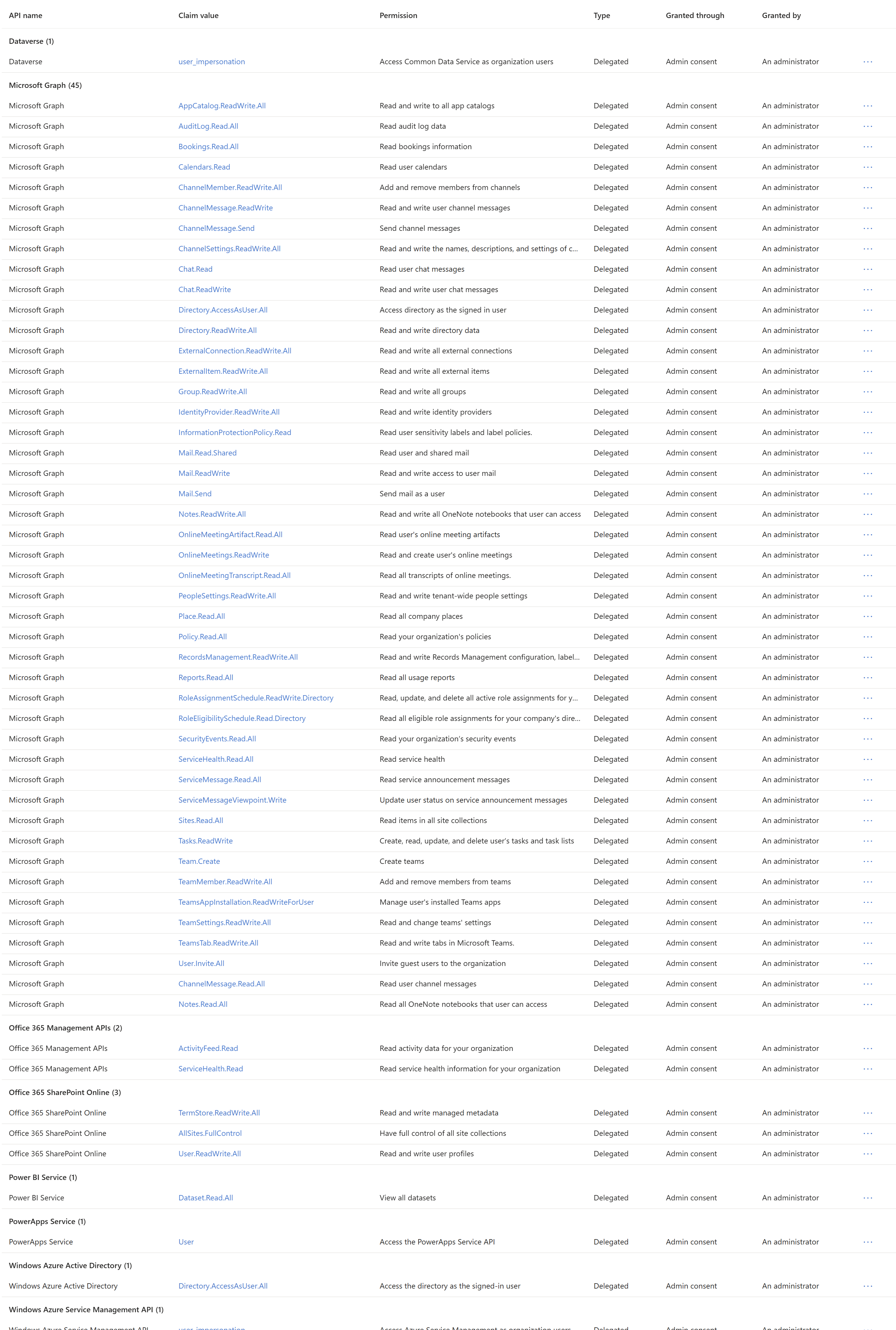
Description of these permissions from the screenshot
Descriptions are burried in the repo of the PnP PowerShell, so I have extracted them here for you to see. For really detailed information on the permissions, you can check out the awesome resource: https://graphpermissions.merill.net/ - I have put a link against each permission to take you to the detailed information to this awesome resource.
Microsoft Graph - Delegated Permissions
| Delegated Permission (claim) | Admin Consent Title & Description |
|---|---|
| AuditLog.Read.All | Read audit log data Allows the app to read and query your audit log activities, on behalf of the signed-in user. |
| Bookings.Read.All | Read bookings information Allows an app to read bookings appointments, businesses, customers, services, and staff on behalf of the signed-in user. |
| Calendars.Read | Read user calendars Allows the app to read events in user calendars . |
| ChannelMember.ReadWrite.All | Add and remove members from channels Add and remove members from channels, on behalf of the signed-in user. Also allows changing a member’s role, for example from owner to non-owner. |
| ChannelMessage.Read.All | Read user channel messages Allows an app to read a channel’s messages in Microsoft Teams, on behalf of the signed-in user. |
| ChannelMessage.ReadWrite | Read and write user channel messages Allows the app to read and write channel messages, on behalf of the signed-in user. This doesn’t allow the app to edit the policyViolation of a channel message. |
| ChannelMessage.Send | Send channel messages Allows an app to send channel messages in Microsoft Teams, on behalf of the signed-in user. |
| ChannelSettings.ReadWrite.All | Read and write the names, descriptions, and settings of channels Read and write the names, descriptions, and settings of all channels, on behalf of the signed-in user. |
| Chat.Read | Read user chat messages Allows an app to read 1 on 1 or group chats threads, on behalf of the signed-in user. |
| Chat.ReadWrite | Read and write user chat messages Allows an app to read and write 1 on 1 or group chats threads, on behalf of the signed-in user. |
| Directory.AccessAsUser.All | Access directory as the signed in user Allows the app to have the same access to information in the directory as the signed-in user. |
| Directory.ReadWrite.All | Read and write directory data Allows the app to read and write data in your organization’s directory, such as users, and groups. It does not allow the app to delete users or groups, or reset user passwords. |
| ExternalConnection.ReadWrite.All | Read and write all external connections Allows the app to read and write all external connections on behalf of a signed-in user. The signed-in user must be an administrator. |
| ExternalItem.Read.All | Read items in external datasets Allow the app to read external datasets and content, on behalf of the signed-in user. |
| Group.ReadWrite.All | Read and write all groups Allows the app to create groups and read all group properties and memberships on behalf of the signed-in user. Additionally allows group owners to manage their groups and allows group members to update group content. |
| IdentityProvider.ReadWrite.All | Read and write identity providers Allows the app to read and write your organization’s identity (authentication) providers’ properties on behalf of the user. |
| InformationProtectionPolicy.Read | Read user sensitivity labels and label policies. Allows an app to read information protection sensitivity labels and label policy settings, on behalf of the signed-in user. |
| Mail.Read.Shared | Read user and shared mail Allows the app to read mail a user can access, including their own and shared mail. |
| Mail.ReadWrite | Read and write access to user mail Allows the app to create, read, update, and delete email in user mailboxes. Does not include permission to send mail. |
| Mail.Send | Send mail as a user Allows the app to send mail as users in the organization. |
| Notes.Read.All | Read all OneNote notebooks that user can access Allows the app to read OneNote notebooks that the signed-in user has access to in the organization. |
| Notes.ReadWrite.All | Read and write all OneNote notebooks that user can access Allows the app to read, share, and modify OneNote notebooks that the signed-in user has access to in the organization. |
| OnlineMeetingArtifact.Read.All | Read user’s online meeting artifacts Allows the app to read online meeting artifacts on behalf of the signed-in user. |
| OnlineMeetings.ReadWrite | Read and create user’s online meetings Allows the app to read and create online meetings on behalf of the signed-in user. |
| OnlineMeetingTranscript.Read.All | Read all transcripts of online meetings. Allows the app to read all transcripts of online meetings, on behalf of the signed-in user. |
| PeopleSettings.ReadWrite.All | Read and write tenant-wide people settings Allows the application to read and write tenant-wide people settings on behalf of the signed-in user. |
| Place.Read.All | Read all company places Allows the app to read your company’s places (conference rooms and room lists) for calendar events and other applications, on behalf of the signed-in user. |
| Policy.Read.All | Read your organization’s policies Allows the app to read your organization’s policies on behalf of the signed-in user. |
| RecordsManagement.ReadWrite.All | Read and write Records Management configuration, labels, and policies Allows the application to create, update and delete any data from Records Management, such as configuration, labels, and policies on behalf of the signed-in user. |
| Reports.Read.All | Read all usage reports Allows an app to read all service usage reports on behalf of the signed-in user. Services that provide usage reports include Office 365 and Azure Active Directory. |
| RoleAssignmentSchedule.ReadWrite.Directory | Read, update, and delete all active role assignments for your company’s directory Allows the app to read and manage the active role-based access control (RBAC) assignments for your company’s directory, on behalf of the signed-in user. This includes managing active directory role membership, and reading directory role templates, directory roles and active memberships. |
| RoleEligibilitySchedule.Read.Directory | Read all eligible role assignments for your company’s directory Allows the app to read the eligible role-based access control (RBAC) assignments for your company’s directory, on behalf of the signed-in user. This includes reading directory role templates, and directory roles. |
| SecurityEvents.Read.All | Read your organization’s security events Allows the app to read your organization’s security events on behalf of the signed-in user. |
| ServiceHealth.Read.All | Read service health Allows the app to read your tenant’s service health information on behalf of the signed-in user. Health information may include service issues or service health overviews. |
| ServiceMessage.Read.All | Read service announcement messages Allows the app to read your tenant’s service announcement messages on behalf of the signed-in user. Messages may include information about new or changed features. |
| ServiceMessageViewpoint.Write | Update user status on service announcement messages Allows the app to update service announcement messages’ user status on behalf of the signed-in user. The message status can be marked as read, archive, or favorite. |
| Sites.Read.All | Read items in all site collections Allows the application to read documents and list items in all site collections on behalf of the signed-in user |
| Tasks.ReadWrite | Create, read, update, and delete user’s tasks and task lists Allows the app to create, read, update, and delete the signed-in user’s tasks and task lists, including any shared with the user. |
| TeamMember.ReadWrite.All | Add and remove members from teams Add and remove members from teams, on behalf of the signed-in user. Also allows changing a member’s role, for example from owner to non-owner. |
| TeamSettings.ReadWrite.All | Read and change teams’ settings Read and change all teams’ settings, on behalf of the signed-in user. |
| TeamsTab.ReadWrite.All | Read and write tabs in Microsoft Teams. Read and write tabs in any team in Microsoft Teams, on behalf of the signed-in user. This does not give access to the content inside the tabs. |
| User.Invite.All | Invite guest users to the organization Allows the app to invite guest users to the organization, on behalf of the signed-in user. |
Office 365 SharePoint Online - Delegated Permissions
| Delegated Permission (claim) | Admin Consent Title & Description |
|---|---|
| TermStore.ReadWrite.All | Read and write managed metadata Allows the app to read, create, update, and delete managed metadata and to read basic site info on behalf of the signed-in user. |
| AllSites.FullControl | Have full control of all site collections Allows the app to have full control of all site collections on behalf of the signed-in user. |
| User.ReadWrite.All | Read and write user profiles Allows the app to read and update user profiles and to read basic site info on behalf of the signed-in user. |
Office 365 Management APIs - Delegated Permissions
| Delegated Permission (claim) | Admin Consent Title & Description |
|---|---|
| ActivityFeed.Read | Read activity data for your organization Allows the application to read activity data for your organization. |
| ServiceHealth.Read | Read service health information for your organization Allows the application to read service health information for your organization. |
Power BI Service - Delegated Permissions
| Delegated Permission (claim) | Admin Consent Title & Description |
|---|---|
| Dataset.Read.All | View all datasets The app can view all datasets for the signed in user and any datasets that the user has access to. |
Power Apps Service - Delegated Permissions
| Delegated Permission (claim) | Admin Consent Title & Description |
|---|---|
| User | Access the PowerApps Service API Accesses all routes in the PowerApps Service API. |
Windows Azure Active Directory - Delegated Permissions
| Delegated Permission (claim) | Admin Consent Title & Description |
|---|---|
| Directory.AccessAsUser.All | Access directory as the signed in user Allows the app to have the same access to information in the directory as the signed-in user. |
Getting more technical information with the Graph Explorer
You can use the Graph Explorer to get more information about the permissions and the API Permissions for details on the app itself BEFORE 9th September. Service Principals filtered to PnP Management Shell | Graph Explorer
You will need to ensure the Graph Explorer is set to the correct tenant and you have consented to Directory.Read.All as a minimum to see the information.
Resources
There are some great resources to help you navigate this change:
Documentation:
- PnP PowerShell - Connecting to SharePoint Online
- CLI for Microsoft 365 - Connecting to SharePoint Online
Community Blogs and resources:
- Creating a PnP.PowerShell App Registration with PowerShell | Todd Klindt Blog
- Microsoft Graph Permissions Explorer
Resources are evolving and I will update this post as more information becomes available. Follow #PnPAppChange handle on X or LinkedIn for the latest updates.
Enjoy!